
Photo credit: LINE/Unsplash.
This is the last article in a three-part series exploring LINE’s technology and the trends it reveals about chat applications. We previously explored how LINE views the future of chat apps, and their newest bot technology. This week, we explore how LINE’s engineering team keeps the app secure.
Instant messaging apps are an attractive target for malicious attacks. Understandably so — much of our lives are poured into our conversations with others, including our whereabouts, private information, and photographs.
That’s why securing a chat app is tough. Chat apps are incredibly multi-faceted and are often equipped with VoIP capabilities, voice messages, app-integrated games, payment functions, and media storage.
One such app is LINE. Fresh off the IPO boat, the subsidiary of the Naver Corporation boasts 220 million users. This means that they have a wealth of personal data, all stored within the company’s internal servers.
To support the many new features that LINE has introduced since their IPO, LINE has expended significant resources to construct a scalable architecture that not only supports these features but protects the information transacted each day.
Meet LEGY
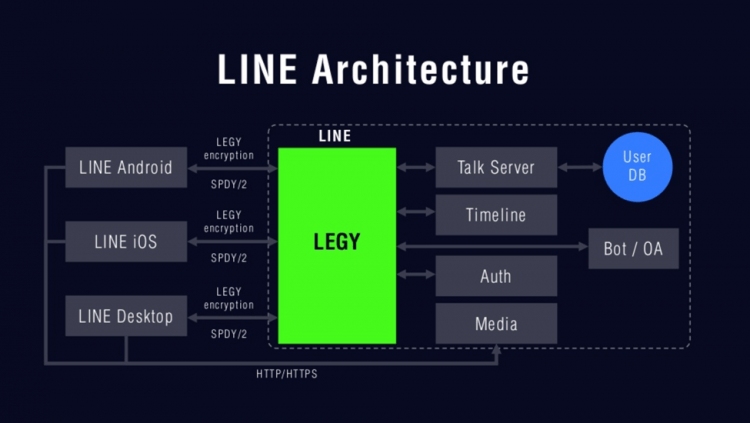
At the heart of LINE’s architecture is the Line Event-delivery GatewaY (or LEGY), a custom-built API gateway server that ensures that everyone can use LINE no matter the device or platform.
LEGY (lovingly named, according to the company’s engineering blog), was created to support the application-layer protocol SPDY (pronounced speedy) used by the app to safely and efficiently transport messages between users. While LINE used to rely on HTTP to transmit messages, SPDY is now the default transport protocol because it guarantees minimal latency. LINE’s transport encryption is layered on top of SPDY.
Employing SPDY also allows multiple requests to be sent in parallel with responses received out of order to enable the feel of a normal back-and-forth conversation. In comparison, HTTP typically creates a new connection for each request, which both increases latency and puts a considerable load on the server.
SPDY’s ping feature also enables LINE to check connection health.
End-to-end encryption
In October 2015, LINE offered end-to-end encryption (E2EE) as an opt-in feature for private text messages. E2EE ensures that neither potential eavesdroppers nor LINE can decode (or decrypt) an encrypted conversation.
Each message is encrypted with a key generated using the Elliptic Curve Diffie-Hellman (ECDH) key agreement protocol. ECDH guarantees that the shared message encryption key can only be derived by users who have access to the key. Thanks to ECDH, each message is encrypted with a unique, random key.
Messaging uses dedicated, per-user static ECDH keys; in contrast, voice calls are encrypted by ephemeral ECDH keys, which are generated only when a call begins and discarded once the call ends.
LINE also uses a True Delete function, which overwrites deleted messages with zeros to ensure that they can’t be restored.
Risk Assessment for games
Anyone familiar with game production will understand how treacherous game hackers can be. That’s why part of a platform’s security measures exist to assess risk from hacks. Though not exactly a security risk, gamers often worm their way past an app’s mechanics to manipulate the game. Game hacking will not only discourage players; it could also affect the app’s revenue stream from in-app items. The level of risk to a platform is hard to assess, so it’s important that the server can recognize dishonest players.
While the client handles status data such as attack power and health points (HP), the server side performs bot/abuser detection, automating the processing and risk assessment of breaches.
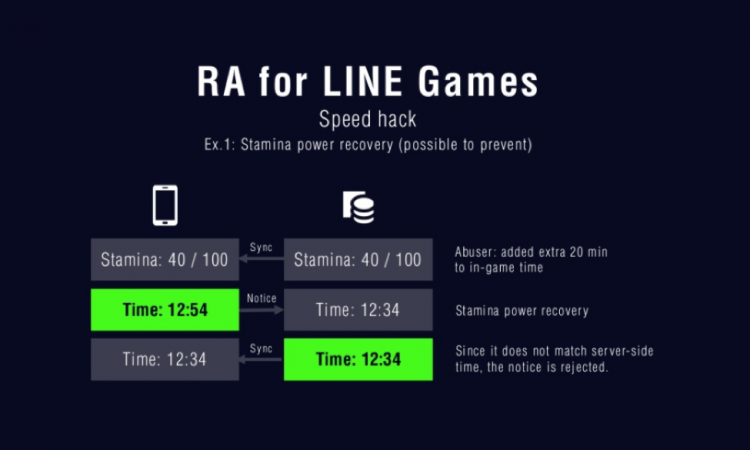
As a security measure, LINE’s engineering team uses significant characteristics to detect anomalies, while also considering false positives. One important metric is time: how long it takes to level up, clear a stage, or process payment can alert the team to possible bot usage or a man-in-the-middle attack.
For example, a common hack to recover in-game stamina is to add an extra 20 minutes to in-game time. However, syncing with the server will reveal that the stamina recovery time doesn’t match the time passed on the server, which makes the server reject the notice.
Crowdsourcing security

What makes LINE’s security exciting to watch is that they’re very open with their improvement efforts; it’s outlined clearly in their engineers’ blog posts and their encryption white paper.
Being open goes a long way in the developer community. As the open-source community has shown, the culture of learning from each other’s experiences and progression goes a long way to improving your abilities and products. It is for this very reason that LINE set up their bug bounty program, encouraging outside developers to test their security and identify problem areas for a cash reward. To date, nine people have entered the Hall of Fame, and four security researchers have received cash rewards.
“When looking at the long term, there is value in crowdsourcing solutions to security issues,” says Naohisa Ichihara, a security engineer at LINE. “Engineers from outside of our company bring a different point of view when looking at things and can quickly find problems that are not as obvious to our resources.”
Moving forward, LINE plans to improve their authentication process, strengthen data protection, and increase abuse-prevention measures. They know well that security measures need to constantly adapt to new forms of attacks. End-to-end encryption may be the new gold standard today, but this may change. Hopefully, so will the security teams.
This post How LINE’s engineering team does security appeared first on Tech in Asia.
from Tech in Asia https://www.techinasia.com/lines-engineering-team-security
via IFTTT
No comments:
Post a Comment