
Indian security firm Fallible claims to have exposed major security flaws in Go-Jek – Indonesia’s highest valued startup on record and a rival of Grab and Uber in the country. Go-Jek claims the issues have been fixed.
Fallible revealed its discoveries in a blogpost on Hackernoon. It specializes in detecting flaws in API end-points – the interface tech companies set up so that other services can exchange data with them. If not secured properly, APIs can lead to leaks, where private data can be extracted in unintended ways.
Fallible claims it was still able to extract ride history data and customer order data a few days ago.
In the case of Go-Jek, Fallible says, it was able to extract information from a ride history API which let it read a list of all rides taken by any user, including GPS coordinates of the ride.
The security firm also claims to have been able to exploit a vulnerability to see details of orders customers made through the app. It even found a way to potentially meddle with notifications users receive.
Another problematic API revealed user data, including phone numbers, pickup and drop off points – but this leak has now been patched, Fallible tells Tech in Asia.
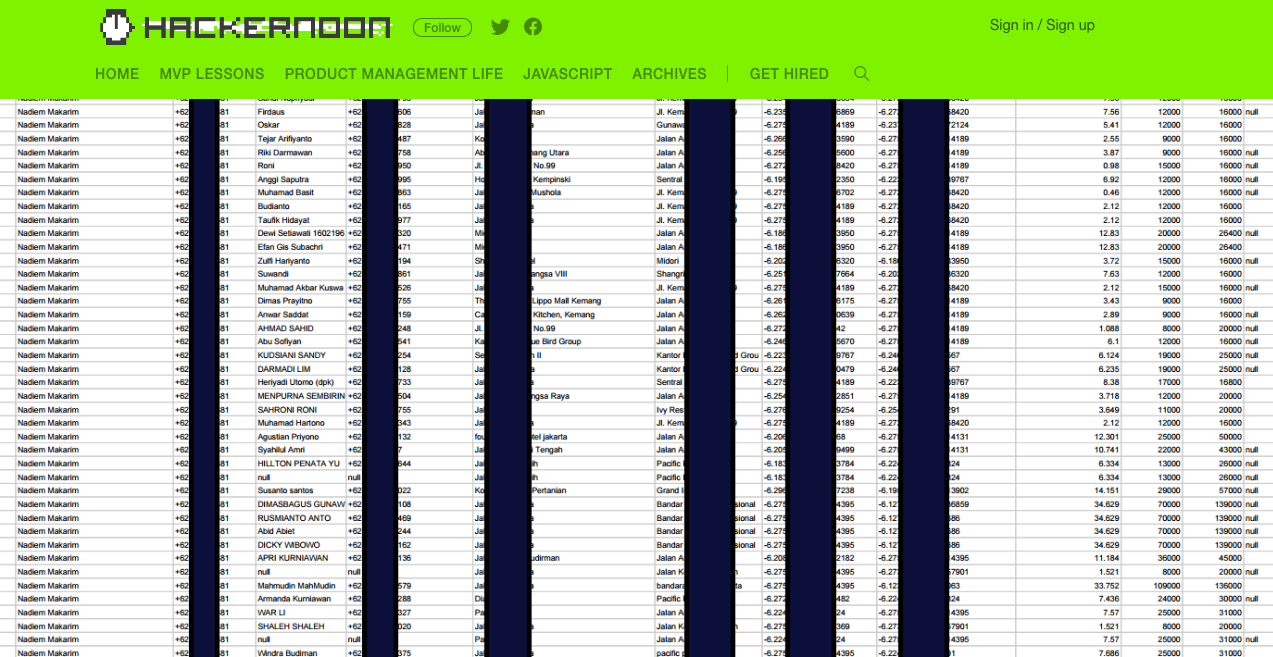
Indian security firm Fallible revealed some of the data it was able to obtain in an article on Hackernoon.
The others were still supposedly pending at the time the Indian firm decided to publish its findings a few days ago, after giving Go-Jek several months to address its security flaws.
Disagreement over what’s been fixed
Go-Jek chief information security officer Sheran Gunasekera argues a different timeline.
He says the data leaks were all addressed and fixed at the end of July, shortly after Fallible first contacted the firm in June.
“I am not claiming we are perfect, but we take the protection of our customer’s data seriously,” says Sheran.
Having worked in information security for 15 years, he agrees it’s a common industry practice to hunt for flaws in big tech companies like Go-Jek. He values the type of responsible disclosure Fallible did.
The way Fallible documented the case could have been better, though, Sheran argues. “The post is nonspecific, it usually comes with more technical specifications, which issues are still open and which are closed.”
Sheran points out that Go-Jek runs a bug bounty program, which invites hackers to find bugs and report them to Go-Jek in return for a reward.
Go-Jek will also release its own blogpost in response to Fallbile, Sheran says.
This is not the first time Go-Jek has been called out on security issues. In early January 2016, an Indonesian programmer based in Thailand made similar disclosures, saying that he believed there were still many bugs left to be revealed in the Go-Jek app.
Security issues with Go-Jek are a serious concern now that the startup is evolving into a payments company. Go-Pay lets users purchase credits and store them in the app for future purchases. More recently, the startup began trialing Go-Pay credit transfers from one user to another and cash withdrawals at partner banks.
Fallible hopes the incident will raise awareness about the importance of data protection.
“In our experience, companies operating in markets with better data security and privacy laws put more investment, like developer time and money, in security due to fear of penalties and lawsuits. Unfortunately, this is not happening in Southeast Asia, including Indonesia. It is high time people who use these services are made aware of these data leaks and their impact.”
This post Go-Jek’s app has major data leaks, claims security firm. Go-Jek says they’re fixed. appeared first on Tech in Asia.
from Tech in Asia https://www.techinasia.com/indian-firm-exposes-go-jek-data-leaks
via IFTTT
No comments:
Post a Comment